Introduction to CipherTrust
CipherTrust is an advanced data security platform developed by Thales that provides organizations with robust encryption, key management, and access controls. It helps enterprises secure sensitive data across on-premises, cloud, and hybrid environments, ensuring compliance with regulations such as GDPR, HIPAA, PCI DSS, and more.
A successful CipherTrust deployment involves careful planning, integration, and configuration to protect critical assets while ensuring seamless operation.
Key Components of CipherTrust
Before diving into the deployment process, it's essential to understand the primary components of the CipherTrust Data Security Platform (CDSP):
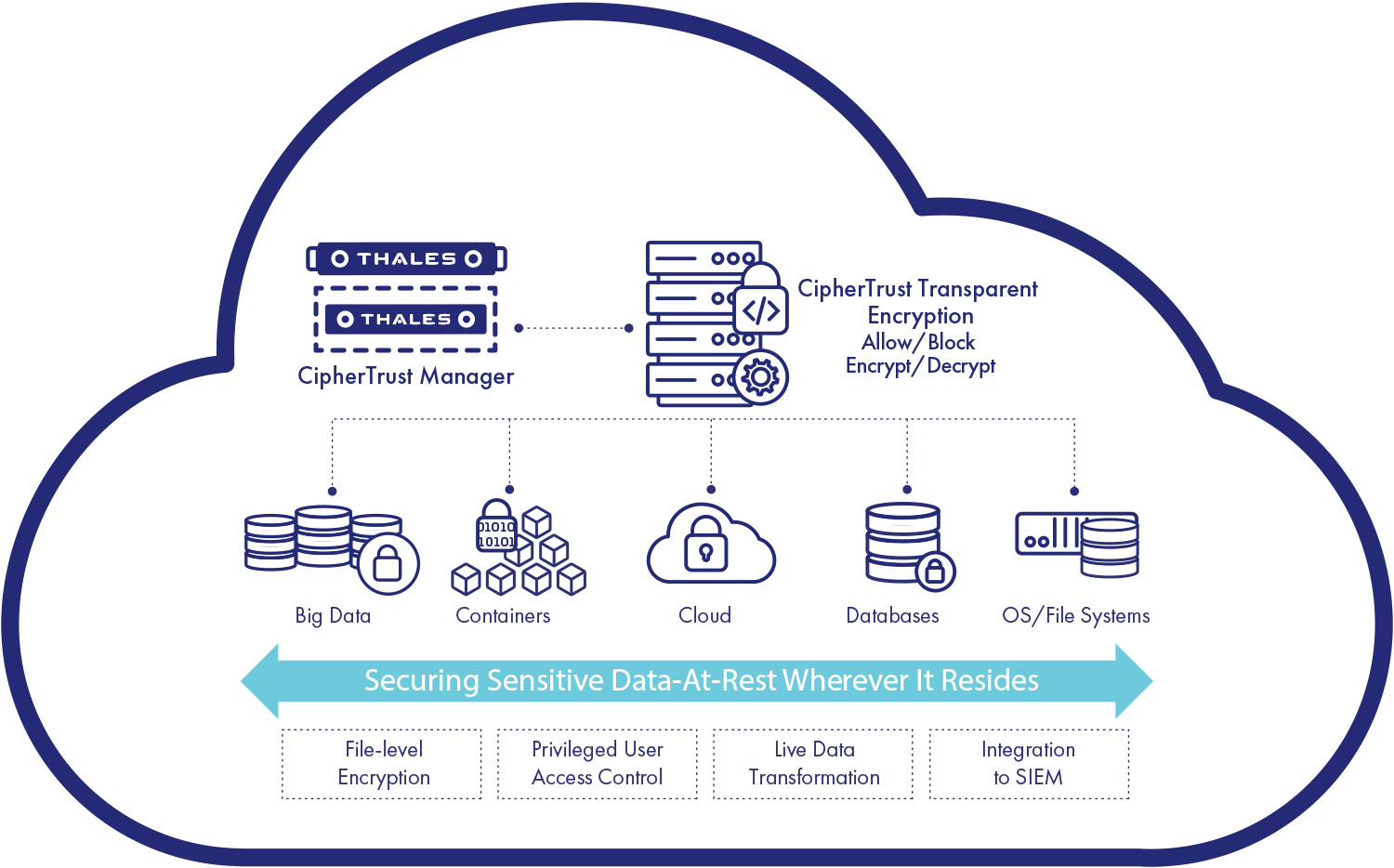
- CipherTrust Manager (CM) – The central management console for encryption key management, policy enforcement, and user access control.
- CipherTrust Transparent Encryption (CTE) – Enables data-at-rest encryption with policy-based access control.
- CipherTrust Cloud Key Manager (CCKM) – Provides centralized control over encryption keys across multiple cloud providers (AWS, Azure, Google Cloud).
- CipherTrust Application Data Protection (CADP) – Enables application-level encryption and tokenization.
- CipherTrust Database Protection – Encrypts sensitive database records with minimal impact on performance.
- CipherTrust Key Management – Manages and secures encryption keys from various third-party sources, including HSMs (Hardware Security Modules).
Steps for CipherTrust Deployment
1. Pre-Deployment Planning
A well-structured deployment starts with careful planning:
- Assess Data Security Requirements: Identify what data needs protection and where it resides (on-premises, cloud, or hybrid).
- Define Compliance Needs: Ensure the solution meets regulatory standards such as FIPS 140-2, GDPR, and PCI DSS.
- Infrastructure Assessment: Evaluate the current IT environment, including servers, databases, applications, and cloud providers.
- Deployment Model Selection: Choose between physical appliance, virtual machine, or cloud-based deployment for CipherTrust Manager.
2. Installing CipherTrust Manager
CipherTrust Manager is the core component that must be deployed first. It can be installed in the following ways:
- On-Premises: Deploy as a virtual appliance on VMware, Hyper-V, or KVM.
- Cloud-Based: Available in AWS, Microsoft Azure, and Google Cloud.
- Hardware Appliance: Install as a dedicated on-premises physical security appliance.
Installation Steps:
- Download and deploy the CipherTrust Manager image.
- Assign network configurations (IP address, DNS, firewall rules).
- Access the CipherTrust Manager Web UI using a browser.
- Set up an administrator account and configure role-based access controls (RBAC).
- Configure backup and recovery policies.
3. Configuring Key Management
- Create and import encryption keys for applications, databases, and cloud storage.
- Set up role-based policies to define key access permissions.
- Integrate CipherTrust Manager with existing HSMs (such as Luna HSM) for additional security.
- Automate key rotation and expiration alerts.
4. Deploying CipherTrust Transparent Encryption (CTE)
CTE is a critical feature that enables file-level encryption and access control for structured and unstructured data.
Steps for Deploying CTE:
- Install the CipherTrust Transparent Encryption agent on target servers.
- Define encryption policies for files, folders, and databases.
- Configure granular access controls based on user roles, processes, and file types.
- Test access restrictions to ensure only authorized users can view decrypted data.
5. Integrating CipherTrust with Cloud Providers
CipherTrust Cloud Key Manager (CCKM) enables secure key management for cloud environments.
Integration Steps:
- Connect CipherTrust Manager to AWS KMS, Azure Key Vault, or Google Cloud KMS.
- Import or generate encryption keys within CipherTrust Manager.
- Enforce policies to restrict unauthorized access to cloud-stored data.
- Set up key lifecycle management for automatic renewal and revocation.
6. Implementing CipherTrust Application Data Protection (CADP)
CADP provides API-based encryption and tokenization for application developers.
Steps to Deploy CADP:
- Install the CipherTrust SDK and APIs in your application.
- Integrate with CipherTrust Manager for encryption key retrieval.
- Encrypt sensitive application data before storage or transmission.
- Configure tokenization for masking sensitive data fields like credit card numbers, SSNs, and personal identifiers.
7. Monitoring and Auditing
CipherTrust offers logging, auditing, and reporting features to ensure security compliance.
Key Monitoring Actions:
- Enable real-time logging and integrate with SIEM (Splunk, IBM QRadar, ArcSight) for event tracking.
- Set up alerts for unauthorized access attempts or policy violations.
- Generate compliance reports for GDPR, HIPAA, and PCI DSS audits.
8. Ongoing Maintenance and Optimization
After deployment, it's essential to continuously monitor and optimize CipherTrust performance.
- Regular Key Rotation: Automate key expiration and renewal.
- Policy Updates: Adjust encryption policies as data and user access patterns change.
- Software Updates: Apply patches and updates to keep CipherTrust secure and up to date.
Benefits of Deploying CipherTrust
- Centralized Encryption and Key Management across hybrid environments.
- Seamless Integration with HSMs, Cloud, and Enterprise Applications.
- Compliance with Global Regulations (GDPR, HIPAA, PCI DSS).
- Granular Access Control to prevent unauthorized data exposure.
- Scalable Security for on-premises and cloud workloads.
Conclusion
Deploying CipherTrust is a strategic move for enterprises looking to strengthen their data security posture. By implementing strong encryption, centralized key management, and robust access controls, organizations can safeguard sensitive data, achieve regulatory compliance, and protect against security breaches. Whether securing on-premises infrastructure or cloud environments, a well-planned CipherTrust deployment ensures data protection, business continuity, and reduced security risks.